In this tutorial I'll tell you how to control your raspberry pi from your smartphone. So follow below tutorial and say good bye to monitor,keyboard and mouse.
Requirements:
1)Raspberry Pi
2)Wi-Fi adapter
3)Smartphone with Wi-Fi Hotspot feature (I would be using Android in this tutorial)
Tutorial:-
Step 1) First install Raspbian OS in SD card and connect SD card to your PC
Step 2) Raspberry Pi Configuration :
-Open SD card using file manager as shown in this SS:-
-Now open terminal and change directory to SD card location like this :-
cd /media/c1398422-7a7c-4863-8a8f-45a1db26b4f2
-Now run below commands :-
Command 1:
sudo echo "
auto wlan0
iface lo inet loopback
iface eth0 inet dhcp
iface default inet dhcp
iface wlan0 inet dhcp
allow-hotplug wlan0
wpa-conf /etc/wpa_supplicant/wpa_supplicant.conf">etc/network/interfaces
Command 2:
sudo echo "
ctrl_interface=DIR=/var/run/wpa_supplicant GROUP=netdev
update_config=1
network={
ssid="mynetworkname"
psk="mypassword"
proto=RSN
key_mgmt=WPA-PSK
pairwise=CCMP
auth_alg=OPEN
}">etc/wpa_supplicant/wpa_supplicant.conf
NOTE:- Replace ssid and psk values with your actual ssid and password.
Step 4) Wi-Fi Hotspot configuration in your smartphone:
-Go to settings and give your desired network SSID and password but make sure to replace "mynetworkname" and "mypassword" with your network SSID and password.
-Now insert SD card and connect Wi-Fi adapter then start your Raspberry Pi
-Now after few seconds and you will get a connection from Raspberry Pi to your smartphone like below:
-Note down the IP address (192.168.43.8)
Step 5)SSH Client Configuration:
- Install JuiceSSH in your android (or if you don't have android then install any supported SSH client and configure it and run)
- Now using SSH client (JuiceSSH) connect to IP address of raspberry pi which we got in step 4 using default credentials-
Username:- pi
Password:- raspberry
JuiceSSH Guide:-
a)Open JuiceSSH and click on thunder like icon located at top right corner and enter your Raspberry Pi details like this:
b)Now type the password as "raspberry"
d)Now you are ready to send your commands to your raspberry Pi ;)
Step 6)Installing VNC on Raspberry :-
-Run below commands:-
Command 1 :- sudo apt-get update
Command 2 :- sudo apt-get install tightvncserver
-Now start vnc server by this command and enter new password if asked:-
sudo vncserver:1
Here 1 is port number ,you can give any unreserved port number.
-You can reset your password by :-
sudo vncpasswd
-That's it.
Step 6)Installing VNC Client in your smartphone :-
-Download and install VNC viewer in your android and run it.
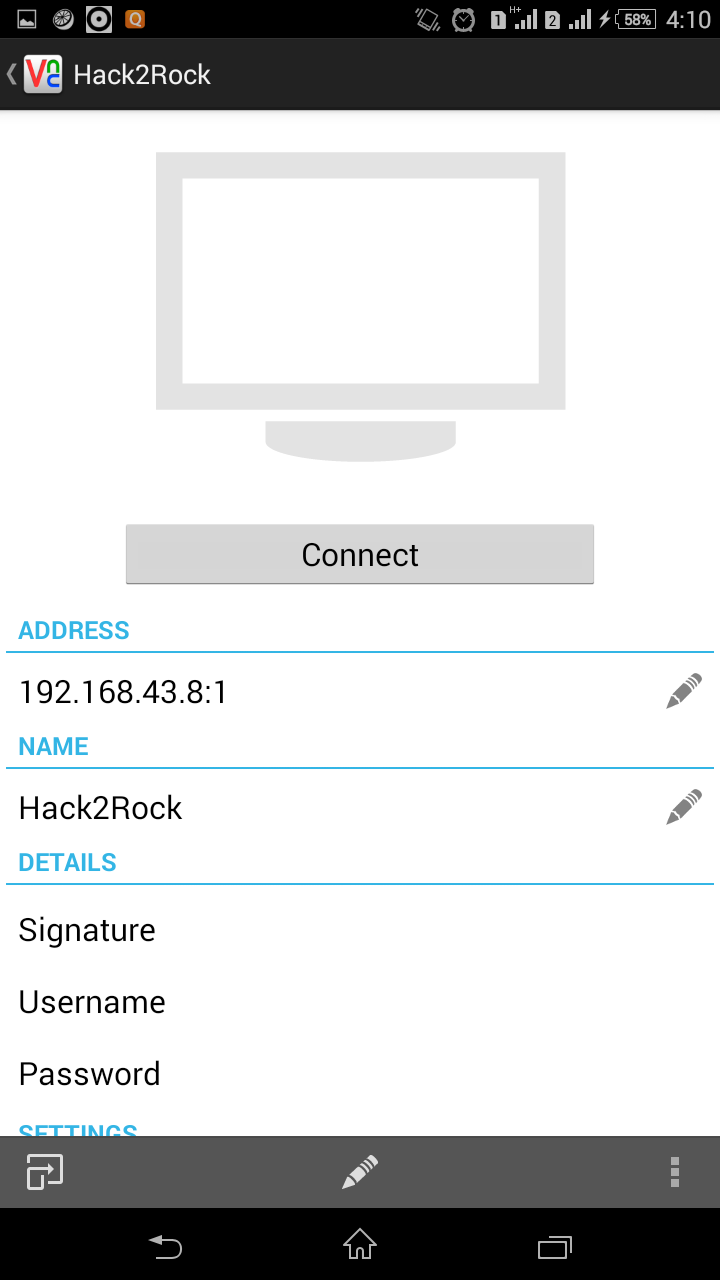
-Now enter address in ip:port format and give any desired name.
For example:- 192.168.43.8:1
Here 192.168.43.8 is my raspberry pi IP address and 1 is port number on which VNC server is listening.
Got any problem?
Ask in comments :)
References:-
http://gettingstartedwithraspberrypi.tumblr.com/post/24142374137/setting-up-a-vnc-server
http://itfixed.blogspot.com/2009/05/how-to-change-vnc-server-password-on.html
Requirements:
1)Raspberry Pi
2)Wi-Fi adapter
3)Smartphone with Wi-Fi Hotspot feature (I would be using Android in this tutorial)
Tutorial:-
Step 1) First install Raspbian OS in SD card and connect SD card to your PC
Step 2) Raspberry Pi Configuration :
-Open SD card using file manager as shown in this SS:-
-Now press Ctrl+L and copy the location as show in this SS:-
-Now open terminal and change directory to SD card location like this :-
cd /media/c1398422-7a7c-4863-8a8f-45a1db26b4f2
-Now run below commands :-
Command 1:
sudo echo "
auto wlan0
iface lo inet loopback
iface eth0 inet dhcp
iface default inet dhcp
iface wlan0 inet dhcp
allow-hotplug wlan0
wpa-conf /etc/wpa_supplicant/wpa_supplicant.conf">etc/network/interfaces
Command 2:
sudo echo "
ctrl_interface=DIR=/var/run/wpa_supplicant GROUP=netdev
update_config=1
network={
ssid="mynetworkname"
psk="mypassword"
proto=RSN
key_mgmt=WPA-PSK
pairwise=CCMP
auth_alg=OPEN
}">etc/wpa_supplicant/wpa_supplicant.conf
NOTE:- Replace ssid and psk values with your actual ssid and password.
Step 4) Wi-Fi Hotspot configuration in your smartphone:
-Go to settings and give your desired network SSID and password but make sure to replace "mynetworkname" and "mypassword" with your network SSID and password.
-Now insert SD card and connect Wi-Fi adapter then start your Raspberry Pi
-Now after few seconds and you will get a connection from Raspberry Pi to your smartphone like below:
-Note down the IP address (192.168.43.8)
Step 5)SSH Client Configuration:
- Install JuiceSSH in your android (or if you don't have android then install any supported SSH client and configure it and run)
- Now using SSH client (JuiceSSH) connect to IP address of raspberry pi which we got in step 4 using default credentials-
Username:- pi
Password:- raspberry
JuiceSSH Guide:-
a)Open JuiceSSH and click on thunder like icon located at top right corner and enter your Raspberry Pi details like this:
Here "pi" is default username of Raspberry Pi SSH and "192.168.43.8" is IP address which we got in step 4.
c)Now click on "Accept"
d)Now you are ready to send your commands to your raspberry Pi ;)
Step 6)Installing VNC on Raspberry :-
-Run below commands:-
Command 1 :- sudo apt-get update
Command 2 :- sudo apt-get install tightvncserver
-Now start vnc server by this command and enter new password if asked:-
sudo vncserver:1
Here 1 is port number ,you can give any unreserved port number.
-You can reset your password by :-
sudo vncpasswd
-That's it.
Step 6)Installing VNC Client in your smartphone :-
-Download and install VNC viewer in your android and run it.
-Now enter address in ip:port format and give any desired name.
For example:- 192.168.43.8:1
Here 192.168.43.8 is my raspberry pi IP address and 1 is port number on which VNC server is listening.

Now just click on connect and enter password when asked and you are ready to go.
Got any problem?
Ask in comments :)
References:-
http://gettingstartedwithraspberrypi.tumblr.com/post/24142374137/setting-up-a-vnc-server
http://itfixed.blogspot.com/2009/05/how-to-change-vnc-server-password-on.html









This comment has been removed by a blog administrator.
ReplyDeleteYou have written a useful thing.It will be helpful for me.Thanks for sharing with us.
ReplyDeletethanku
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteKya re noob kya comment daala tha? xD
Delete